Enabling Entra ID Authentication on Linux Virtual Machines
Integrating Entra ID (formerly Azure Active Directory) authentication into Linux Virtual Machines (VMs) can significantly streamline access management by enabling centralized identity-based access control. This article walks through the process of enabling Entra ID authentication for a Linux VM in Azure, outlines the necessary Terraform configurations, and discusses common pitfalls encountered during implementation.
Step 1: Enable System-Assigned Identity for the VM
Before any Entra ID-based authentication can be configured, the Linux VM must have a system-assigned managed identity. This identity allows the VM to interact securely with Azure services.
identity {
type = "SystemAssigned"
}
This block should be included in your azurerm_linux_virtual_machine resource definition in your Terraform configuration.
Its also a standard convention across all Terraform resources that support Managed Identity — either System Assigned or User Assigned — although the type value is prone to be inconsistent.
Step 2: Add the AADSSHLogin Extension
To enable Entra ID login capability, the appropriate VM extension must be added. This extension handles the necessary plumbing to integrate Entra ID with the SSH login process.
resource "azurerm_virtual_machine_extension" "aad_login" {
name = "${azurerm_linux_virtual_machine.vm1.name}/AADSSHLogin"
virtual_machine_id = azurerm_linux_virtual_machine.vm1.id
publisher = "Microsoft.Azure.ActiveDirectory"
type = "AADSSHLoginForLinux"
type_handler_version = "1.0"
}
Step 3: Assign Login Permissions to the Current User
To grant yourself or other users login access, retrieve the current user’s object ID and assign the appropriate role.
data "azurerm_client_config" "current" {}
Assign the “Virtual Machine User Login” role to the current user:
resource "azurerm_role_assignment" "aad_vm_user_login" {
scope = azurerm_linux_virtual_machine.vm1.id
role_definition_name = "Virtual Machine User Login"
principal_id = data.azurerm_client_config.current.object_id
}
If admin-level access is needed, assign the “Virtual Machine Administrator Login” role instead:
resource "azurerm_role_assignment" "aad_vm_admin_login" {
scope = azurerm_linux_virtual_machine.vm1.id
role_definition_name = "Virtual Machine Administrator Login"
principal_id = data.azurerm_client_config.current.object_id
}
Step 4: SSH Using Azure Bastion with Entra ID
Once the above configurations are in place, you can attempt to connect to the VM using Azure Bastion and Entra ID authentication:
az network bastion ssh \
--name "bas-network-dev" \
--resource-group "rg-network-dev" \
--target-resource-id "/subscriptions/<subscription-id>/resourceGroups/rg-linuxvm-dev/providers/Microsoft.Compute/virtualMachines/vm1linuxvmdev" \
--auth-type "AAD"
Note: Replace
with your actual subscription ID.
Troubleshooting: Common Errors and Solutions
Invalid Resource ID Error
During connection attempts, you may encounter the following error:
Please enter a valid resource ID. If this is not working, try opening the JSON view of your resource (in the Overview tab), and copying the full resource ID.
I follow the instructions just to be sure I am using the right Resource ID and I didn’t fat finger something along the way.
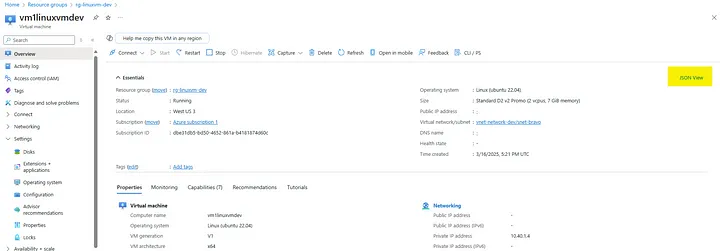
Finding the “JSON View” link in the upper right hand corner of the VM. The Resource ID is easily identifiable from the JSON payload displayed.
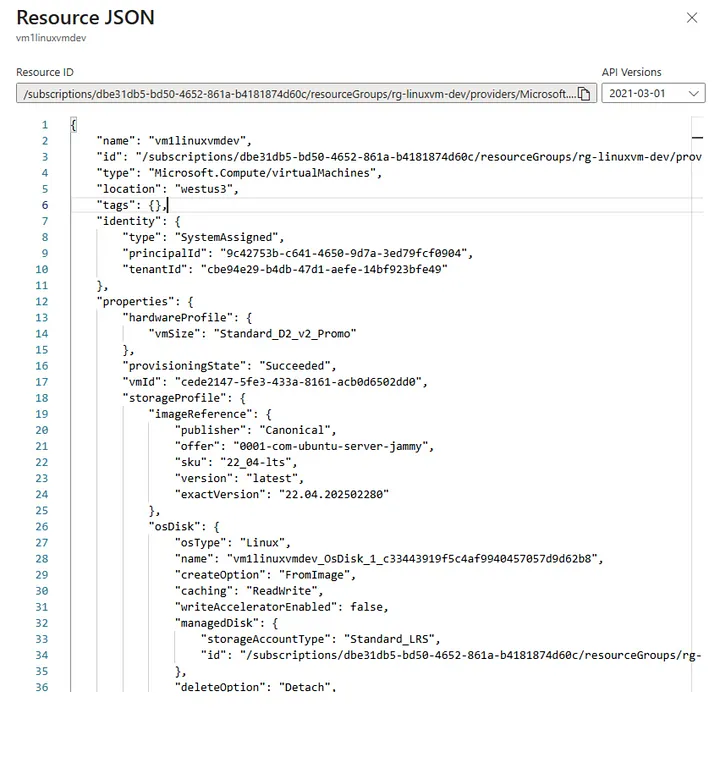
Even after verifying the resource ID using the “JSON View” link in the Azure portal, the error may persist. Ensure that the ID matches exactly, without extra spaces or characters. For reference, a valid resource ID should look like this:
/subscriptions/<subId>/resourceGroups/rg-linuxvm-dev/providers/Microsoft.Compute/virtualMachines/vm1linuxvmdev
SSH Timeout Error Using Azure CLI
When attempting to connect via:
az ssh vm -n vm1linuxvmdev -g rg-linuxvm-dev
You might receive this warning and error:
I get the following warning and subsequent error: No public IP detected, attempting private IP (you must bring your own connectivity). Use — prefer-private-ip to avoid this message. OpenSSH_for_Windows_9.5p1, LibreSSL 3.8.2 ssh: connect to host 10.40.1.4 port 22: Connection timed out
It turns out there is an issue with this from Git Bash. The same command works from the Windows Command Line.
az network bastion ssh \
--name "bas-network-dev" \
--resource-group "rg-network-dev" \
--target-resource-id "/subscriptions/dbe31db5-bd50–4652–861a-b4181874d60c/resourceGroups/rg-linuxvm-dev/providers/Microsoft.Compute/virtualMachines/vm1linuxvmdev" \
--auth-type "AAD"
Conclusion
Enabling Entra ID authentication for Linux VMs provides a secure and manageable access mechanism, especially in enterprise environments where centralized identity control is critical.
While the Terraform setup is relatively straightforward, nuances such as the correct use of resource IDs, network connectivity, and command-line environments can introduce complications.
With proper role assignments and awareness of the common pitfalls, you’ll be able to streamline Entra ID-based SSH access to your VMs effectively.