Disabling Default Outbound Network Access in Azure Subnets with Terraform
When working with Azure virtual networks, managing the flow of traffic to and from your subnets is a critical part of securing your infrastructure. By default, Azure allows outbound internet access from subnets even when no specific route is defined. This behavior is controlled by a setting known as Default Outbound Access, which can be enabled or disabled depending on your security requirements.
The Need to Disable Default Outbound Access
For environments that prioritize strict egress controls — such as those requiring explicit outbound access via NAT gateways, Azure Firewall, or custom user-defined routes — it’s essential to disable the default outbound access. Leaving this enabled can introduce unintended exposure to the internet and undermine security policies.
Many companies are rolling out policies to enforce this setting — so its a good idea to get a head start by learning where this setting is managed and how to automate it with Terraform.
The Portal Experience
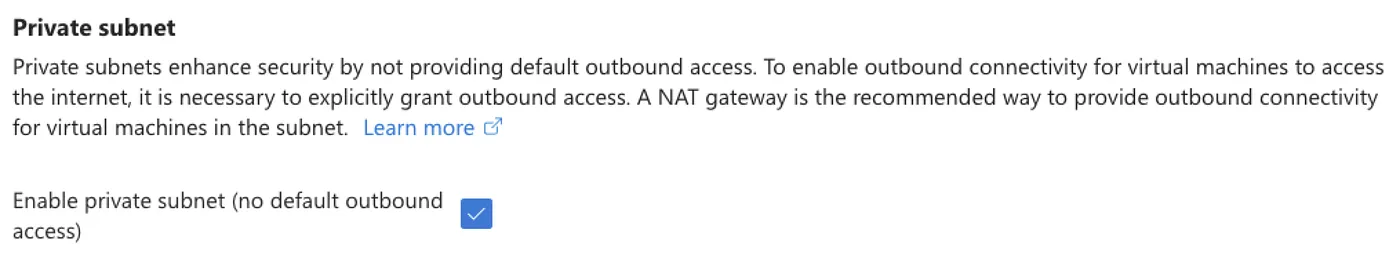
In the Azure Portal, this setting is found by editing the subnet configuration. Scroll past the IP address range section to locate a checkbox labeled Default outbound access. Unchecking this box will disable the automatic internet access.
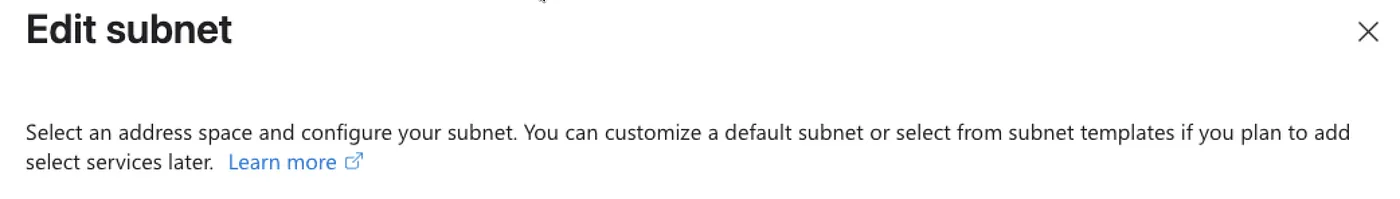
It’s this checkbox further down the blade below the IP address range.
Implementing in Terraform
To disable the default outbound access for a subnet in Terraform, you can use the default_outbound_access_enabledproperty within the azurerm_subnet resource. This flag allows you to explicitly turn off outbound internet access unless routed otherwise.
Here’s an example configuration:
resource "azurerm_subnet" "default" {
name = "default"
resource_group_name = azurerm_resource_group.main.name
virtual_network_name = azurerm_virtual_network.main.name
address_prefixes = [local.subnet_address_space]
default_outbound_access_enabled = false
}
This snippet defines a subnet named default within the specified resource group and virtual network. The key line, default_outbound_access_enabled = false, ensures that the subnet will not have outbound internet access by default.
It’s kind of weird that the Terraform resources says “Enabled = false” while the Azure Portal says “Disabled = true” — yet another odditity in the design of the Azure Portal vs. the Azure Terraform provider.
However, if you are trying to lock down your network security — do not forget it!